
Login Into Your Account

Reset Password
Law enforcement Technology,Law enforcement Agency,Policing Technology,Smart Policing India,Homeland Security India,Border Security India,Border Management India,Cyber Crime news,Cyber Security news,Safety App,Public Safety App,Security App,Women Safety App,Police Initiative,Surveillance news,National Security news,isc event 2016,isc event 2017,scada event 2016,scada event 2017,Critical infrastructure security event 2016,Critical infrastructure security event 2017,iot summit 2016,iot summit 2017,Internet of things seminar 2016,Internet of things seminar 2017,iot seminar delhi 2016,iot seminar delhi 2017,iot conference delhi 2016,iot conference delhi 2017,top security event,security event,security event 2016,security event 2017,security conference 2016,security conference 2017,cso summit 2016,cso summit 2017,Corporate security event,Corporate security conference,security research india,homeland security research india,security think tank india
Law enforcement Technology,Law enforcement Agency,Policing Technology,Smart Policing India,Homeland Security India,Border Security India,Border Management India,Cyber Crime news,Cyber Security news,Safety App,Public Safety App,Security App,Women Safety App,Police Initiative,Surveillance news,National Security news,isc event 2016,isc event 2017,scada event 2016,scada event 2017,Critical infrastructure security event 2016,Critical infrastructure security event 2017,iot summit 2016,iot summit 2017,Internet of things seminar 2016,Internet of things seminar 2017,iot seminar delhi 2016,iot seminar delhi 2017,iot conference delhi 2016,iot conference delhi 2017,top security event,security event,security event 2016,security event 2017,security conference 2016,security conference 2017,cso summit 2016,cso summit 2017,Corporate security event,Corporate security conference,security research india,homeland security research india,security think tank india

How Russia recruited elite hackers for its cyberwar
Vyarya, 33, a bearded, bespectacled computer programmer who thwarted hackers, said he was suddenly being asked to join a sweeping overhaul of the Russian military last year. Under a new doctrine, the nation’s generals were redefining war as more than a contest of steel and gunpowder, making cyberwarfare a central tenet in expanding the Kremlin’s interests.
"Sorry, I can’t," Vyarya said he told an executive at a Russian military contracting firm who had offered him the hacking job. But Vyarya was worried about the consequences of his refusal, so he abruptly fled to Finland last year, he and his former employer said. It was a rare example of a Russian who sought asylum in the face of the country’s push to recruit hackers.
"This is against my principles — and illegal," he said of the Russian military’s hacking effort.
While much about Russia’s cyberwarfare program is shrouded in secrecy, details of the government’s effort to recruit programmers in recent years — whether professionals like Vyarya, college students or even criminals — are shedding some light on the Kremlin’s plan to create elite teams of computer hackers.
U.S. intelligence agencies say that a team of Russian hackers stole data from the Democratic National Committee during the presidential campaign. On Thursday, the Obama administration imposed sanctions against Russia for interfering in the election, the bedrock of the U.S. political system.
The sanctions take aim at Russia’s main intelligence agencies and specific individuals, striking at one part of a sprawling cyberespionage operation that also includes the military, military contractors and teams of civilian recruits.
For more than three years, rather than rely on military officers working out of isolated bunkers, Russian government recruiters have scouted a wide range of programmers, placing prominent ads on social media sites, offering jobs to college students and professional coders, and even speaking openly about looking in Russia’s criminal underworld for potential talent.
Those recruits were intended to cycle through military contracting companies and newly formed units called "science squadrons," established on military bases around the country.
As early as 2013, Sergei Shoigu, the Russian defense minister, told university rectors at a meeting in Moscow that he was on a "head hunt in the positive meaning of the word" for coders.
The Defense Ministry bought advertising on Vkontakte, Russia’s most popular social network. One video shows a man clanging a military rifle on a table beside a laptop computer, then starting to type.
"If you graduated from college, if you are a technical specialist, if you are ready to use your knowledge, we give you an opportunity," the ad intoned. Members of the science squadrons, the video said, live in “comfortable accommodation,” shown as an apartment furnished with a washing machine.
University students subject to mandatory conscription in the nation’s armed forces, but who wanted to avoid brutal stints as enlistees, could opt instead to join a science squadron. A government questionnaire asks draftees about their knowledge of programming languages.
The ministry posted openings on job forums, according to an investigation by Meduza, a Russian news site based in Riga, Latvia, that first disclosed the recruitment effort. One post from 2014 advertised for a computer scientist with knowledge of "patches, vulnerabilities and exploits," which refers to sabotage used to alter a computer.
Given the size of Russia’s cybercrime underworld, it was not long before the military considered recruiting those it delicately described as "hackers who have problems with the law."
In an article titled "Enlisted Hacker" in Rossiiskaya Gazeta, the government newspaper, a deputy minister of defense, Gen. Oleg Ostapenko, said the science squadrons might include hackers with criminal histories. "From the point of view of using scientific potential, this is a matter for discussion," he was quoted as saying in 2013.
Experts say the strategy was more than just talk.
"There have been cases where cybercriminals are arrested but never ended up in prison," said Dmitri Alperovitch, the co-founder and chief technology officer of CrowdStrike, the cybersecurity company that first identified the group known as Fancy Bear as the perpetrator of the Democratic National Committee hacking.
Vyarya, the programmer who turned down the government’s job offer, was an attractive recruit from the opposite end of the spectrum: someone with a career protecting people against hackers.
Specifically, he had experience shielding websites from a maneuver called a distributed denial of service, or DDoS attack, in which the sites are overwhelmed and disabled by a torrent of fake traffic. Among his clients were Vedomosti, an independent newspaper; TV Rain, an opposition-leaning television station; and the website of Aleksei Navalny, the opposition leader.
Vyarya said that in 2015 he was invited to accompany Vasily Brovko, an executive at the military contracting company Rostec, on a trip to Sofia, Bulgaria. But he said it turned out to be a demonstration of a new software suite capable of staging DDoS attacks.
The Bulgarian firm demonstrating the software briefly crashed the website of Ukraine’s Defense Ministry and Slon.ru, a Russian news website, Vyarya said. Slon has confirmed its site went down inexplicably for about two minutes that day, Feb. 5, 2015.
After the demonstration, Vyarya said Brovko asked him how the program might be improved. Then, according to Vyarya, Brovko offered him a job running the DDoS software, which he said the Russians planned to buy from the Bulgarians for about $1 million.
Vyarya said his problems began when he turned down the offer: He was surveilled, and an acquaintance in law enforcement advised him to flee the country. He left in August 2015 for Finland to seek asylum, he and his former employer said. The Finnish government, citing safety and privacy concerns, would not comment on the asylum application.
"As soon as we saw what was on the table, Sasha was given direct instructions to return to his hotel and stop all contacts," said his former boss, Aleksandr V. Lyamin of Qrator, a cyberdefense company in Moscow, using Vyarya’s Russian nickname. But the overtures from the military contractor persisted, Lyamin said, and Vyarya fled.
Rostec strongly denied Vyarya’s account. Brovko did travel to Bulgaria with Vyarya, the company said, but to evaluate software for defensive, not offensive, cybersystems. A spokeswoman for Brovko called the account of crashing sites in a product demonstration the imagination of a “mentally unstable” man.
The military’s push into cyberwarfare had intensified in 2012, with the appointment of a new minister of defense, Shoigu. The next year, a senior defense official, Gen. Valery Gerasimov published what became known as the Gerasimov Doctrine. It posited that in the world today, the lines between war and peace had blurred and that covert tactics, such as working through proxies or otherwise in the shadows, would rise in importance.
He called it "nonlinear war." His critics called it "guerrilla geopolitics."
But Russia is certainly not alone.
"Almost all developed countries in the world, unfortunately, are creating offensive capabilities, and many have confirmed this," said Anton M. Shingarev, a vice president at Kaspersky, a Russian antivirus company.
Recruitment by Russia’s military should be expected, he said. "You or I might be angry about it, but, unfortunately, it’s just reality. Many countries are doing it. This is the reality."
U.S. intelligence agencies, including the National Security Agency, have for decades recruited on college campuses. In 2015, the NSA offered a free summer camp to 1,400 high school and middle school students, where they were taught the basics of hacking, cracking and cyberdefense.
In Russia, recruiters have looked well beyond the nation’s school system.
In 2013, as Russia’s recruitment drive was picking up, Dmitry A. Artimovich, a soft-spoken physicist, was awaiting trial in a Moscow jail for designing a computer program that spammed email users with advertisements for male sexual enhancement products.
One day a cellmate, convicted of selling narcotics online, sidled up to him with some news. The cellmate said that people incarcerated for cybercrimes could get out before trial, in exchange for working for the government. Another inmate had already taken a deal, he said.
"It was an offer to cooperate," Artimovich said.
"Why else would you work for the government?" he added. "The salaries are tiny. But if you do something illegal, and go to prison for eight or nine years, the FSB can help you," he said, using a Russian abbreviation for the Federal Security Service.
Artimovich said he decided to take his chances at trial, and served a year in a penal colony.
As Russia ramped up its abilities, government agencies were also in the market for surveillance and hacking software, including some from legal suppliers in the West.
In 2014, a Russian company called Advanced Monitoring that has a license to work with the FSB, the agency that succeeded the KGB after the fall of the Soviet Union, bought iPhone hacking software from an Italian company called Hacking Team, according to invoices published by WikiLeaks. Hacking Team has since lost its export license.
Western cybersecurity analysts believe they have identified the one responsible for the breaching the Democratic National Committee: a group nicknamed Fancy Bear.
First known as Advanced Persistent Threat 28, the group has been active since 2007 but its abilities evolved to emphasize attacks, rather than gather intelligence, after the military placed a priority on cyberwarfare.
It stepped up “faketivist” actions that released stolen data through contrived online personalities like Guccifer 2 and websites like DCLeaks, according to Kyle Ehmke, a senior intelligence researcher at ThreatConnect, a cybersecurity company. The group had been called Pawn Storm, named for a chess maneuver. It was nicknamed Fancy Bear in 2014.
This year, the group appropriated the nickname for its own use, setting up the website fancybear.net and publishing hacked data from the World Anti-Doping Agency, which showed that many U.S. athletes including the tennis star Serena Williams had medical exemptions to take banned substances. The hack was apparently in retaliation for revelations of Russian doping in sports.
President Vladimir Putin has said repeatedly, most recently at his annual year-end news conference, that the information released in the recent Democratic National Committee hacks was more important than who was behind them.
"The main thing, to my mind, is the information the hackers provided," Putin said of this summer’s cyberattack.
Democratic Party members and the Obama administration should not look abroad for someone to blame for losing the election, Putin said. "You need to learn how to lose gracefully," he said.

Mine collapses in Jharkand's Lalmatia, seven people killed
A heap of mud caved in at the entry point of the Latmatia mines of Eastern Coalfields Limited (ECL) in Godda district, police said. The collapse occurred at 8:30pm yesterday, the state disaster management department said.
"So far, bodies of seven miners have been recovered from the mine. Rescue work is on," RR Mishra, officiating CMD of ECL, said. Police said two persons were injured in the incident and were being treated at a hospital.
About 40 workers are suspected to be still trapped under the debris.
Several vehicles were also trapped, according to police.
Rescue work started after midnight, the disaster management department said. Four workers have been rescued, and have been admitted in a hospital at Mahagama in Godda. The condition of one of the workers is reportedly serious.
Jharkhand Chief Minister Raghubar Das is closely monitoring the situation, and has asked concerned officials to intensify rescue operations.
"Saddened by the loss of lives at a mine in Jharkhand. My prayers are with those trapped inside. Spoke to CM Raghubar Das on the situation "Modi said on twitter.
Narendra Modi ✔ @narendramodi
Jharkhand Government & Minister @PiyushGoyal are working to restore normalcy. @NDRFHQ has been engaged for rescue & relief operations.
Expressing sorrow, the Jharkhand Chief Minister today announced assistance of Rs two lakh for the families of the miners who died in the accident.
He also announced Rs 25,000 to the injured, official sources said.
"All senior officials have been asked to stay at the site," the CM said on twitter.
Coal India has been requested for a mining rescue station team with specialized equipment.
At the time of the cave-in at the Rajmahal Open Cast Mines of Paharia Bhorya site, more than 70 vehicles were inside.
Rescue operation could not begin due to night fog, the police said.
The National Disaster Response Force (NDRF) team reached around 11am from Patna.
The local police and administration were also involved in the rescue operation.
The Director General of Mines Safety (DGMS) has sent a team to the spot to investigate.

Exclusive: CISF to be the world’s largest aviation security player by 2030, says OP Singh
On various aspects of the security force that guards the economic installations of the country, the CISF’s director-general, OP Singh, a 1983 batch IPS officer of Uttar Pradesh cadre spoke to Firstpost in an exclusive interview. Edited excerpts follow:
Prior to your appointment as CISF chief, you had been the National Disaster Response Force (NDRF) chief and had stints in the CRPF and Special Protection Group (SPG). What challenges do you perceive as director-general of CISF?
I have worked with the CISF earlier and was in charge of 59 airports in the country. But it was only for a year. Working in the paramilitary forces is a challenging task and each (unit) has its own different way of performing its duty and dealing with crises and humanitarian work. CISF was created to secure the industrial environment. After the 1956 industrial policy, the country witnessed the emergence of large public sector undertakings (PSUs) and lots of industries. Following economic liberalisation and globalisation, there was a surge in the industrial sector and security of this sector became paramount. It emerged as a futuristic force, where the need was to secure the most sensitive installations and also those sectors like airports, seaports, Metro rail etc that have a direct impact on our economy. Our role is to protect all these vital economic installations in government, public and private sectors. We’re even protecting heritage sites.
How challenging is it for CISF to secure airports, especially after the Kandahar incident in which IA flight IC-814 was hijacked in 1999?
After the hijacking incident, the government decided to revamp airport security system in a big way, when the need was felt to give the responsibility of securing airports to a professional, dedicated and strong force. CISF was assigned the job and we were given the responsibility of Jaipur airport in 2000. Earlier, it was looked after by the state police. Ever since, aviation security was a new and highly challenging assignment for us.
The aviation sector is growing by leaps and bounds, and by 2020, CISF will be the world’s third largest aviation security expert. We’ll be the largest player in the aviation security market by 2030. Besides, aviation security is regulated by international standards and norms; CISF has to catch up with all these challenges.
CISF director-general OP Singh in his office.
How does CISF safeguard sensitive installations in nuclear and space sectors?
Different treatment is required to protect various domains in the country. Here, technological advancement comes into play and therefore besides manual training, CISF goes for technological training, and gadgets become one of our most important USPs. From securing airports to nuclear plants and space centres, we require hi-tech gadgets. We undergo a high level of technological training combined with our soft and hard skills, physical reflexes, armed training, etc. So, CISF is a conglomeration of all these tools and techniques.
What is CISF’s modernisation plan?
Technology is required in various fields of our functioning. For instance, in access control — which is the know-how required to gain access to a particular installation such as an airport building, or in perimeter security — the area of the airport which is banned for public and is under constant patrolling. You need different gadgets for these specialised jobs. For a quick response time to vulnerable and emergency situations like any terror threat, you need quick response teams to protect installations. Then screening and frisking all require technical gadgets. All CISF personnel, whether working in airports or in different fields, undergo specialised training as per requirement. Securing an airport requires different skills than for securing a nuclear power plant.
CISF wants to provide an integrated security solution under a single umbrella.
Is CISF’s backhand operation equally important?
Of course. We provide training on computerisation, monitoring events via CCTV, post-investigation of incidents, analysis of events etc. On the basis of these, ground-level decisions are taken.
After the Mumbai terror attack (26 November) in 2008, what is CISF's brief in combating terror threats?
After Mumbai, the mandate of the force was broadened to provide security cover to private establishments by amending the CISF Act. We have specialised training for anti-terror activities, which is provided to our people in the training institutes based in Madhya Pradesh and Greater Noida. Then we have VIP security. We conduct mock drills at various installations to measure up our preparedness for any such eventuality.
Is CISF providing security to installations based in the Red Corridor that is home to Naxals?
Yes, in a big way. Our men have risen to the occasion by not only providing security to installations against Left-wing extremism but also in managing a big public domain — by providing safety and security to thousands of staff members working in the industrial sector. Our job is to protect all the economic installations like mines, steel and power plants, gas pipelines, rail tracks, etc in the Red Corridor from the Naxal threat looming over them.
Besides the Red Corridor, CISF is deployed in other sensitive areas in Jammu and Kashmir and North Eastern states to provide security to highly vulnerable and critical establishments.

Ericsson says demonstrated IoT solutions in Andhra Pradesh village
Both projects -- Connected Aquaponics and Smart Water Grid Management -- were demonstrated in the presence of Andhra Pradesh Chief Minister N. Chandrababu Naidu, after a three-month pilot.
Ericsson earlier this year signed a memorandum of understanding (MoU) with the Andhra Pradesh government and the University of California - Berkley to help improve lives of farmers in and around Mori.
"The 'Connected Aquaponics' and 'Smart Water Grid Management' IoT solutions being demonstrated here will help improve harvest and optimise water distribution. It has the potential to provide an improved life for millions of farmers in the country," Anand Varadarajan, head of Ericsson Research, Chennai, at Ericsson India, said in a statement.
The company said that Connected Aquaponics integrates aquaculture and hydroponics for reuse of the ammonia-rich waste water from aquaculture for organic farming and recycle the water back to the aqua farm.
"Using wireless sensor network and Ericsson's AppIOT platform, we enable the monitoring of the aqua farm 24x7, thereby enabling the farmers with real-time information," the company said.
This enables the farmers to increase the yield as well as bring down the production cost with optimum use of the raw materials and repeated use of water.

Cyber security may face threats in days to come: ex-Nasscom chairman
"With the increase in digital connectivity and with demonetisation, cyber security becomes a crucial element for India," a statement quoting Reddy, also the Founder and Executive Chairman, Cyient Limited said today.
"There is an existing requirement of 5 lakh cyber security professionals in India, which will grow in the coming years," Reddy said.
On the IT and ITeS industry trends and prospects in 2017, he said, skilling will play a role in transforming the organisation into digital enterprise and the digital technology which is grouped as SMAC (Social, Mobile, Analytics and Cloud), contributes to 5-10 per cent of the industry revenue. However, it is anticipated that the digital solutions will touch 60 per cent in 5-10 years.
"The incoming new projects will need combination of multiple technologies, and has to be build by smaller teams in shorter cycles. The need will be for multi-skill high performance organisations. To address the changing needs, workforce has to be reskilled more often and needs different approach," he said.
Developing the local markets into a technology consuming market will be a key challenge and the country is yet to be known as technology consuming country.
According to him, the IT industry went through peaks and lows during 2016 on account of volatile political, economic and technological environment globally.
In spite of all the uncertainties, India's market share continues to be at 7 per cent of the global software and IT services spend, and 57 per cent of global IT services is outsourced to India.
The IT BPM industry is poised to grow at 8-10 per cent for the FY 2017, demonstrating sustained growth, he said.

Protection from Tsunami
Dr Satheesh C Shenoi
Where there is a will, there will be a way. India has proven this axiom once more with aplomb.
Cut back to year December 26, 2004, the day world's one of the most devastating disaster struck killing 2,30,000 people in 14 countries along the rim of the Indian Ocean. Massive waves swept away buildings and people as if they were just pieces of paper. The damage was worst in Indonesia, Thailand, India and Sri Lanka. In India, an estimated 10,749 persons lost their life and 5,640 people were reported missing.
The disaster led to much soul searching as it soon became clear that much of the casualty could have been avoided if only there had been an early warning system for tsunamis in the Indian Ocean region. There were two tsunami warning centres at the global level. But, they catered to the pacific region only. Nobody expected a tsunami in the Indian Ocean.
The Tsunami was generated by an undersea earthquake about 250 km south west of the Indonesian city of Banda Aceh and it took anywhere between 15 minutes to seven hours for the fatal waves to reach the various coastlines.
The northern regions of the Indonesian island of Sumatra were hit very quickly. But, east coast of India was affected two hours later and west coast in four hours.
In other words, there was enough time to warn the people in India. Seismologists knew that a massive earthquake with a magnitude of 9.3 on the Richter scale had occurred. But, it was not known that it had generated a tsunami.
As a result, huge tsunami waves swept India, Sri Lanka, Indonesia, Thailand and other countries along the Indian Ocean with no warning what so ever. In India, the coastal communities in Tamil Nadu, Puducherry, Andhra Pradesh, Kerala, and Andaman and Nicobar Islands were devastated.
Since then, the situation has undergone a sea change. Today, a 24X7 early warning system is operational. It has a capability to issue tsunami bulletins in less than 10 minutes after any major earthquake in the Indian Ocean. This provides a response/lead time of about 10 to 20 minutes to regions nearer to the epicentre of the quake and a few hours in the case of regions further away.
The great Indian Ocean tsunami occurred on December 26, 2004 and within a year the Government approved the setting up of an early warning system after detailed brainstorming sessions with experts in the field both within and outside the country. Set up at a cost of Rs. 150 crore, the system became operational on October 15, 2007. Initially, it had a capability to issue a warning within 20 minutes. It has since then been fine tuned and first warning is now available within 10 minutes.
The Indian Tsunami Early Warning System [ITEWS] comprises of a real time network of seismic stations, tsunami buoys and tide gauges. These are linked to a state-of-art tsunami centre – Indian Tsunami Early Warning Centre [ITEWC], where the data are analysed using high power computational systems. Advisories are issued automatically to the various stakeholders beginning from the Ministry of Home Affairs and the National Disaster Management Authority to State and district level disaster management centres for necessary follow up action.
The ITEWC is located at the Union Ministry of Earth Science's Indian National Centre for Ocean Information Services [INCOIS] in Hyderabad.
The real time seismic monitoring network comprises of 17 broadband seismic field stations transmitting real time data through V-SAT communication to the central receiving stations located at INCOIS and the National Centre for Seismology at New Delhi simultaneously for processing and interpretation. In addition, data from around 300 global seismic stations is received at INCOIS in near real time. These data sets form the basis for determining the preliminary parameters of earthquake epicentre, focal depth and magnitude. The earthquakes are auto-located within 5-10 minutes of occurrence.
The brain of the early warning system is a state of the art decision support system at ITEWC, which has a database of all possible earthquake scenarios for the Indian Ocean.
The moment a tsunamigenic earthquake -- an undersea quake with a magnitude of 6.5 and above occurs, the decision support system gets activated and rapidly goes through the database and fishes out the matching advisory.

Top 4 Cyber Attack Vectors of 2016
It is evident that 2016, has been a year filled with all types of cybercrime. Ranging from DDoS attacks to malware, hacking to ransomware, and social engineering to skimming, a lot of havoc has been caused by select groups of individuals. But what were some of the top attack vectors exploited by criminals in 2016?
#4 DDOS ATTACKS ARE GROWING IN NUMBER
The recent attacks against DynDNS go to show how a major denial-of-service attack wave can cripple the Internet as we know it today. But DDoS attacks are becoming more common in general, although not all of them are on the same level as the October 21st attack. Overload or even crashing web servers with a multitude of requests is an effective way to gain glory in the hacker world.
It is rather easy to fight most DDoS attacks in most cases, such as filtering specific traffic types and regions. Moreover, DDoS mitigation is an absolute must for all of the great companies in the world right now. Unfortunately, even the best protection does not mean that hackers won’t find a way to disrupt services.
#3 MALWARE AND RANSOMWARE
Even though the media headlines have been filled with stories about malware and ransomware all year, they are not the big culprit in cyber attacks yet. Granted, the number of malware attacks is growing exponentially, and that trend will continue for some time. Protecting against these intrusions is a top priority, although human error is often to blame for a malware infection.
#2 APPLICATION-SPECIFIC ATTACKS
Albeit his term may sound foreign to a lot of people, application-specific attacks are a prime threat to Internet users. Hackers targeting specific applications is a cause for concern, as it allows them to capture all data packets flowing through that application. For example, a major attack against Skype would put all users’ communications at risk of being leaked. Close to one in five cyber attacks throughout 2016, relied on using application-specific attacks, which is quite a troublesome number.
#1 WEB APPLICATIONS ATTACKS
As most people may have noticed, web applications are becoming a very lucrative target for hackers. In fact, web application attacks have been around for quite some time now. SQL injections, cross-site scripting, and other types of attack are very common. One such attack recently allowed a white hat hacker to obtain sensitive information from UberCENTRAL.
Preventing web applications attacks has been a challenge for security researchers throughout the years. It is up to individual app developers to secure and maintain their code base at all times. Criminals and hackers are always one step ahead in this game, and it is of the utmost importance to even the playing field whenever possible.
If you liked this article, follow us on Twitter @themerklenews and make sure to subscribe to our newsletter to receive the latest bitcoin, cryptocurrency, and technology news.

50 Days Later: Public Safety On-Camera
Public Safety owns 40 body-cameras and every on-duty officer is equipped with a Pro-Vision Body Cam. Each camera is built to be waterproof, is capable of recording at night with infrared illuminators, includes built in microphones and a 170 degree field of vision on top of other specs.
“At first officers were a bit uncomfortable, but as we began using them in training, they adjusted to the change… the camera helps improve the officer’s performance,” said Joseph Marswillo, the Chief of Police at NJIT. The purpose of the camera is not only to hold the police accountable for their actions, but also civilians. Once both parties understand they are being recorded, it can help deescalate the situation and improve the outcomes of interactions.
The process of wearing the cameras was far from easy. Before being issued their body-camera, all officers are required to participate in departmental training. The training consisted of body camera policy review, use of equipment training videos, a policy review PowerPoint / test prep, and a 27 question test.
One of the arguments for body-cameras is that they offer an objective truth instead of the “your word vs theirs” predicament that takes place in most civil suits. Chief Marswillo mentioned, “Most police departments will be adapting body-cameras.” Most towns in New Jersey have already seen law enforcement officers using the cameras and not too long ago did the NJ Attorney General announce a half a million initiative to fund BWCs to be worn throughout state police departments.
With an increasing amount of officers wearing body-cameras, the scope of the visual and audio records is unlike anything before it. Who can see this footage? Just about any citizen of the State of New Jersey, minus a few exceptions.
Under the state’s Open Public Records Act (OPRA), a “record” is deemed as a “document, drawing, plan, photograph, image processed document, information stored or maintained electronically or by sound-recording” that is kept in file in the course of official business by any officer, commission, agency or authority of the state.
NJIT Public Safety worked intensely to come up with a policy of their own for who was allowed to view those records, and the process was anything but simple. By policy, any footage released that is not a part of a criminal investigation, civil discovery or subpoena (a writ ordering a person to court), must first be approved by the Essex County Prosecutor’s Office or Division of Criminal Justice. Body-cam footage can only be stored for at least 90 days according to policy.
Body-cameras blur the line between safety and privacy. While there is accountability for people’s actions, the cost could be something most do not come to think of.
Fortunately, NJIT Public Safety follows a protocol for situations that involve entering private areas, such as a dorm room. Officers are allowed to turn their body camera on when entering a resident’s room, provided they are within the resident’s room for a law enforcement purpose. Officers are required to advise victims and witnesses within the area, if safe and practical to do so, that those parties are being recorded.
The reason for Public Safety adopting body-cameras is to improve their relationship with students and assure their safety. While most students are unaware of the cameras, they do support Public Safety’s decision to use them. “I don’t mind at all. It’s them showing more awareness and gives more safety to us,” mentioned Ashraf Siddique, a fellow NJIT student.
Public Safety has a positive relationship with students as they host at least 3 campus events bonding and showing their good sides. They have more plans to improve their services behind the scenes that deserve praise for going the extra mile to ensure students’ protection and their own liability.

Your Smart Home Could Also Be a Haven for Hackers
Just two months ago, hackers harnessed internet-connected devices, such as video cameras and digital video recorders, in an attack on a key part of the internet's infrastructure. The attack caused internet outages and congestion across a wide swath of the country, according to the tech blog Krebs on Security.
Experts fear internet-connected toasters, refrigerators and thermometers -- collectively called the Internet of Things -- can be conscripted into a virtual army by hackers if companies continue to create products with weak or no security protections.
It's often impossible to know if your devices are insecure. In mid-December, a researcher posted about a vulnerability in several models of Netgear-branded routers could allow hackers to take control.
The U.S. CERT Coordination Center at Carnegie Mellon University rated the flaw as critical. Netgear began rolling out beta patch updates for the device [earlier this month].
Billions of Devices
There are so many IoT devices they will soon rival the number of humans on planet Earth. Information technology research firm Gartner estimates 6.4 billion internet-connected things exist today, which could more than triple to nearly 20.8 billion devices by the year 2020.
These gadgets can exist on the spectrum of fun to absurd. One device allows users to play with their pets via an internet connected camera and a smartphone-controlled laser. Exercise trackers log our steps and our sleep. If you ever felt the need for a Wi-Fi-connected tray that tells you how many eggs you have in the fridge, that exists, too.
With connected devices, our world can be in the palm of our hands. Check temperatures from a smart oral and rectal thermometer from your phone. At the store and not sure if you have enough cheese? This smart refrigerator by Samsung now takes a picture of the contents every time the door is closed. Online retailer Amazon has offered small, Wi-Fi connected devices that order various products with the press of a button -- these are part of the Internet of Things, too.
Some products are really helpful, said Ashish Gupta, chief marketing officer for Infoblox, a Santa Clara, California, technology firm that acquired Tacoma's IID earlier this year.
"We drive up to Tahoe, which is about four hours away, and our house is freezing cold in the winter," Gupta said. Enter the IoT thermostat, which his wife turns on with her smartphone two hours before they arrive. "When we get there, the house is nice and warm."
But novelty and convenience can come at a cost. Device security is not keeping pace with innovation, the Department of Homeland Security wrote in a paper released last month.
"Because our nation is now dependent on properly functioning networks to drive so many life-sustaining activities, IoT security is now a matter of homeland security," the agency wrote.
Devices, harnessed by hackers, were able to shut down the central heating and water systems last month at two apartment buildings in Finland. Last year, researchers found nine types of internet-connected baby monitors were vulnerable. They were able to view live video feeds, change camera settings and copy video clips stored online.
"When you're dealing with things that stream data, whether it's video or audio, to the internet, you have to look at your comfort level of who you are and what do you do," said Deral Heiland, research lead at Rapid7, a company that in part seeks security vulnerabilities and reports them to product creators.
Jason Hong, an associate professor of computer science at Carnegie Mellon University in Pittsburgh, said beefing up security costs money, and companies want to maximize profits.
"A lot of people are rushing to market quickly," Hong said. "It's easy to see this product has a beautiful form factor and user interface. It's hard to see if it's got security built in."
Minimize Risks
Users can take a few simple measures to minimize their risks, Hong and others said:
-- Change the device or service's default passwords. Manufacturers often ship products to consumers with what's called a "factory default setting" with the same password. Changing the password makes it harder for hackers to access.
-- Search online for the product name to see if any security flaws have been found.
-- Unplug devices when they are not being used.
-- Install all software updates for your device. Operating software can be a weak spot in device security.
-- Consider why you need an internet-connected device in the first place.
Companies with decades of experience in other spaces are starting to enter the web-connected device market.
"Automobile companies are starting to realize they are also software companies," Hong said. "Some of them don't realize that -- and that's where the danger is."
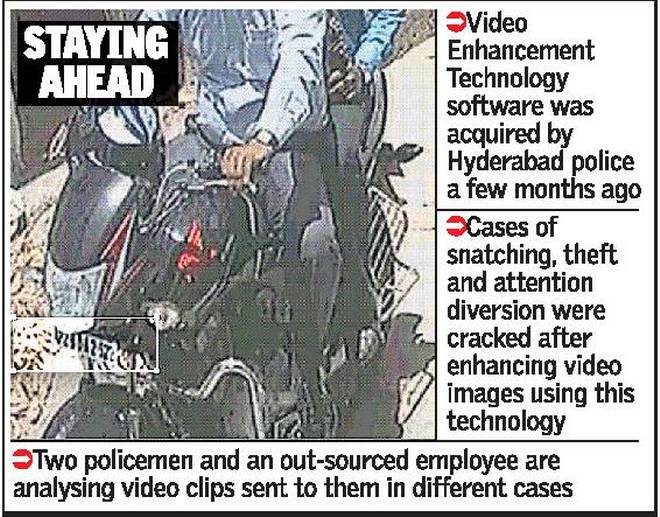
Video enhancing technology helping city police crack cases
Not just the sensational case of gun attack on the banker, several cases of chain snatching were also detected thanks to the VET acquired by Hyderabad police by spending more than Rs. 30 lakh. Video images or clips received by investigators in criminal cases for clues are not of uniform picture quality.
Using different factors like light and color combinations, the VET software improves the images. “Once the video images to be analysed are attached to the VET software, the images become sharper making minute details like digits or letter clearer,” a police officer told The Hindu.
Sharper and brighter images naturally hep in identifying the suspects. The software was acquired by IT Cell of Hyderabad police. Two policemen and an outsourced employee, who is a post-graduate in Forensic Science are analysing such video clips.
As the team gained reputation over passing on crucial clips on video clips, district police units of Telangana and Andhra Pradesh had also approached them for help in similar cases. Video clip of a suspect involved in the kidnap and murder of a software employee from Chennai was sent to
Hyderabad police for analysis.
Info-graphics
*Video Enhancement Technology software was acquired by Hyderabad Police a few months ago.
*Cases of snatching, thefts and attention diversion were cracked after enhancing video images using this technology.
*Two policemen and an out-sources employee (post-graduate in forensic science) are analysing video clips sent to them in different cases.
Newsletter
Sign Up for Monthly Newsletter
Recent Tweets
CONTACT US
Crux Center for Security
Research and Events (CCSRE)
3rd Floor, Tower-B, Unitech Cyber Park
Sector 39, Gurugram,122022
0124- 4207903, 05, 06
Copyright © 2016 Crux Center For Security Research And Events (CCSRE) | All Right Reserved
