
Login Into Your Account

Reset Password
Law enforcement Technology,Law enforcement Agency,Policing Technology,Smart Policing India,Homeland Security India,Border Security India,Border Management India,Cyber Crime news,Cyber Security news,Safety App,Public Safety App,Security App,Women Safety App,Police Initiative,Surveillance news,National Security news,isc event 2016,isc event 2017,scada event 2016,scada event 2017,Critical infrastructure security event 2016,Critical infrastructure security event 2017,iot summit 2016,iot summit 2017,Internet of things seminar 2016,Internet of things seminar 2017,iot seminar delhi 2016,iot seminar delhi 2017,iot conference delhi 2016,iot conference delhi 2017,top security event,security event,security event 2016,security event 2017,security conference 2016,security conference 2017,cso summit 2016,cso summit 2017,Corporate security event,Corporate security conference,security research india,homeland security research india,security think tank india
Law enforcement Technology,Law enforcement Agency,Policing Technology,Smart Policing India,Homeland Security India,Border Security India,Border Management India,Cyber Crime news,Cyber Security news,Safety App,Public Safety App,Security App,Women Safety App,Police Initiative,Surveillance news,National Security news,isc event 2016,isc event 2017,scada event 2016,scada event 2017,Critical infrastructure security event 2016,Critical infrastructure security event 2017,iot summit 2016,iot summit 2017,Internet of things seminar 2016,Internet of things seminar 2017,iot seminar delhi 2016,iot seminar delhi 2017,iot conference delhi 2016,iot conference delhi 2017,top security event,security event,security event 2016,security event 2017,security conference 2016,security conference 2017,cso summit 2016,cso summit 2017,Corporate security event,Corporate security conference,security research india,homeland security research india,security think tank india

After Tesla and Google, now Apple to launch self-driving car
According to a report in The Verge, the Cupertino-based tech giant -- under its so-called Project Titan -- has submitted a letter to the National Highway Traffic Safety Administration, stating that it is "investing heavily in the study of machine learning and automation, and is excited about the potential of automated systems in many areas, including transportation".
The letter is Apple's official comment on the federal government's automated vehicle guidelines, released last September.
Interestingly, Apple's letter is signed by Steven Kenner -- the company's head of product integrity who up until recently was the global director of automotive safety at Ford.
"Apple agrees that companies should share de-identified scenario and dynamics data from crashes and near-misses. By sharing data, the industry will build a more comprehensive dataset than any one company could create alone," Kenner's letter was quoted as saying.
Recently reports surfaced suggesting that the company is not attempting to build its own electric car but is focused on developing self-driving software it can deploy in partnership with existing carmakers.
"This letter comes amid news that hundreds of members of Apple's 1,000-employee-strong car team have been reassigned, let go, or have left of their own volition," the report pointed out.
In October, Uber ordered 100 self-driving vehicles from the Swedish company Volvo.
The news came after an 18-wheeler self-driving Volvo trailer drove from Fort Collins, Colorado, to Colorado Springs, bearing 50,000 cans of Budweiser beer.
The Volvo truck, equipped with cameras and sensors, was owned by Otto, a self-driving truck company acquired by Uber earlier this year.

Common QR code for payments: Here's how it will help vendors
How will it work? A merchant will display the common QR code, which can be scanned using a smartphone app linked to any of the three payments networks — RuPay, MasterCard and Visa — and the money will be directly transferred by a buyer to the merchant's account. Such QR-code based payments will not require a physical card.
While Paytm, which has gone all-out to acquire merchants, also allows payments using a QR code, it is a closed-loop system. What it means is that only Paytm members can transact and money travels within its network. However, the government's interoperable QR code-based solution will allow payments through multiple gateways.
The push for an interoperable QR code has come following a brainstorming session between major banks, payments companies and government officials led by Piyush Goyal, minister of state for power, coal and renewable energy. The interoperable QR code-based payments solution is being called India QR for now, and is targeted to be launched in January.
Visa has been a pioneer in QR Code payments, having developed and launched mVisa in India in Bengaluru over a year ago. mVisa has now been picked up in different markets across the world. Soon after Visa, Paytm launched its QR code app for offline merchants. MasterCard has just launched its solution — Masterpass QR service — which debuted in Ratnakar Bank-partnered Ongo payment wallet. RuPay is expected to launch its own QR code solution shortly.
nowadays QR code is used before that I hardly see anyone using QR codes

Nine innovative technologies that made a mark
2016, too, was no different. From a pocket-sized drone to Solarcity Gigafactory, it was the year of cutting-edge, futuristic technologies. Here's a recap of the most important tech innovations that caught our fancy this year.
Apple AirPods
In its annual September gig, Apple once again proved that it's ahead of the times as it launched the wireless earbuds. Typical Apple white earbuds, sans the cords, these come armed with a five-hour battery life and can be charged through a case. Flanked by microphones, these do not get messy as there is no untangling of the wires, and, also have Siri on call with a simple double tap.
Pokemon Go
The free augmented reality mobile game managed to kill many couch potatoes, as the quest for Pikachu became a craze. Millions ditched their work and other commitments to throng the streets in search of the characters to catch via their Android/iOS app. The Niantic's viral game Pokemon Go lets you catch the virtual characters in real-life environment and uses real-time geospatial technologies and Google map date to play. Traffic disruptions, accidents, visits to the temple - Pokemon Go did it all! With 25 million downloads on July 14 and a record 75 million downloads in just 19 days, it hit a crest, and then receded.
Snapchat Spectacles
Snapchat made its hardware debut this year with a set of spectacles that had a built-in video camera, armed with a 115-degree, wide angle lens. The first wearable designed especially for the Snapchat generation, this one looks hipster enough and it enables recording content from a human eye perspective. A button on the left records a 10-second clip - and the LED bar on the frame lights up to indicate that a video recording is on (avoids covert recording). Connected with the smartphone via Blutooth or WiFi, content gets automatically added to Snapchat's Memories section. What's more - it also can record a full day's worth of video clips on a single charge!
Amazon Echo
Amazon gave us its Bluetooth speaker, which is more than a virtual assistant like Apple's Siri or Microsoft's Cortana. The smart home appliance has Alexa embedded in it and the speaker can talk back to you. With Echo, Amazon made it easier to book a cab via Uber, order pizza and even turn off the lights of your house. The tech team at Amazon is still working on making it more intuitive, and expect an improved one in 2017!
Light phone
If you got tired of your smartphone being intrusive, there was hope rekindled this year. The Light Phone was launched to rescue all smartphone junkies from their addiction. The Brooklyn based company Light Phone developed a credit card-sized device that helped to disconnect one from one's smartphone. A 2G Nano SIM card, a battery life of three weeks on a single charge and a dot matrix LED display that doubles up as a torch, this one was dubbed as 'phone away from phone'. At $100, it also boasts of a touch module, microphone and a Micro-USB port. Mind you, it doesn't support internet and has no camera - clearly taking the detox thing seriously!
Wynd
This intelligent portable air purifier surfaced in 2016 to remove all the contaminants from your immediate surroundings. The tiny purifier can detect and automatically filter out dust, allergens, smoke, and pollution wherever you take it. The device track and display air quality trends over time and it gives a real-time air quality map using sensors from other Wynd devices around the world.
Playstation VR
Move over, flat screens and video games. Sony's Playstation VR offer gamers a whole new way to experience their favourite games. The £349 Playstation VR measures about 187×185×277 mm and weighs 610g, excluding the cable. It has a 5.7-inch OLED screen with a 1920 x 1080 resolution, split across both eyes, providing roughly 100-degree field of view. There's a six-axis motion sensing system and nine LEDs that let the PlayStation's camera tell where players are even when they're turned away from it.
DJI Mavic Drone
DJI's Mavic Pro is a pocket-sized drone that fits in the palm of your hand. It features a 4K camera, obstacle-avoidance technology and the ability to track objects when it is flying. Unlike the bulky drones, the Mavic drone can fold down till its size is similar to that of a loaf of bread. Its ability to fold down makes its less susceptible to accidents.
Solarcity Gigafactory
The Solarcity Gigafactory is a solar panel manufacturing plant which will produce 10,000 solar panels per day and has an estimated cost of $750 million. The dream project of Elon Musk will ensure highly efficient solar cells made at a lower price. The factory stretches for about 6 million square feet, or the equivalent of 126 acres. The giant factory will help it dramatically cut the cost of its batteries by "using economies of scale, innovative manufacturing, reduction of waste, and the simple optimization of locating most manufacturing process under one roof." Once the factory is fully operational by 2020, Tesla estimates the factory will enable it to reduce its battery prices by about 30%. The lowered cost of the batteries will enable the company to price its Model 3 at about $35,000.

Researchers Find Fresh Fodder for IoT Attack Cannons
A Sony IPELA camera. Image: Sony.
A Sony IPELA camera. Image: Sony.
In a blog post published today, Austrian security firm SEC Consult said it found two apparent backdoor accounts in Sony IPELA Engine IP Cameras — devices mainly used by enterprises and authorities. According to SEC Consult, the two previously undocumented user accounts — named “primana” and “debug” — could be used by remote attackers to commandeer the Web server built into these devices, and then to enable “telnet” on them.
Telnet — a protocol that allows remote logons over the Internet — is the very same communications method abused by Mirai, which constantly scours the Web for IoT devices with telnet enabled and protected by factory-default passwords.
“We believe that this backdoor was introduced by Sony developers on purpose (maybe as a way to debug the device during development or factory functional testing) and not an ‘unauthorized third party’ like in other cases (e.g. the Juniper ScreenOS Backdoor, CVE-2015-7755),” SEC Consult wrote.
It’s unclear precisely how many Sony IP cameras may be vulnerable, but a scan of the Web using Censys.io indicates there are at least 4,250 that are currently reachable over the Internet.
“Those Sony IPELA ENGINE IP camera devices are definitely reachable on the Internet and a potential target for Mirai-like botnets, but of course it depends on the network/firewall configuration,” said Johannes Greil, head of SEC Consult Vulnerability Lab. “From our point of view, this is only the tip of the iceberg because it’s only one search string from the device we have.”
Greil said there are other undocumented functionalities in the Sony IP cameras that could be maliciously used by malware or miscreants, such as commands that can be invoked to distort images and/or video recorded by the cameras, or a camera heating feature that could be abused to overheat the devices.
Sony did not respond to multiple requests for comment. But the researchers said Sony has quietly made available to its users an update that disables the backdoor accounts on the affected devices. However, users still need to manually update the firmware using a program called SNC Toolbox.
Greil said it seems likely that the backdoor accounts have been present in Sony cameras for at least four years, as there are signs that someone may have discovered the hidden accounts back in 2012 and attempted to crack the passwords then. SEC Consult’s writeup on their findings is available here.
In other news, researchers at security firm Cybereason say they’ve found at least two previously unknown security flaws in dozens of IP camera families that are white-labeled under a number of different brands (and some without brands at all) that are available for purchase via places like eBay and Amazon. The devices are all administered with the password “888888,” and may be remotely accessible over the Internet if they are not protected behind a firewall. KrebsOnSecurity has confirmed that while the Mirai botnet currently includes this password in the combinations it tries, the username for this password is not part of Mirai’s current configuration.
But Cybereason’s team found that they could easily exploit these devices even if they were set up behind a firewall. That’s because all of these cameras ship with a factory-default peer-to-peer (P2P) communications capability that enables remote “cloud” access to the devices via the manufacturer’s Web site — provided a customer visits the site and provides the unique camera ID stamped on the bottom of the devices.
Although it may seem that attackers would need physical access to the vulnerable devices in order to derive those unique camera IDs, Cybereason’s principal security researcher Amit Serper said the company figured out a simple way to enumerate all possible camera IDs using the manufacturer’s Web site.
“We reverse engineered these cameras so that we can use the manufacturer’s own infrastructure to access them and do whatever we want,” Serper said. “We can use the company’s own cloud network and from there jump onto the customer’s network.”
Lior Div, co-founder and CEO at Cybereason, said a review of the code built into these devices shows the manufacturer does not appear to have made security a priority, and that people using these devices should simply toss them in the trash.
“There is no firmware update mechanism built into these cameras, so there’s no way to patch them,” Div said. “The version of Linux running on these devices was in some cases 14 years old, and the other code libraries on the devices are just as ancient. These devices are so hopelessly broken from a security perspective that it’s hard to really understand what’s going on in the minds of people putting them together.”
Cybereason said it is not disclosing full technical details of the flaws because it would enable any attacker to compromise them for use in online attacks. But it has published a few tips that should help customers determine whether they have a vulnerable device. For example, the camera’s password (888888) is printed on a sticker on the bottom of the devices, and the UID — also printed on the sticker — starts with one of these text strings:
textstrings
The sticker on the bottom of the camera will tell you if the device is affected by the vulnerability. Image: Cybereason.
The sticker on the bottom of the camera will tell you if the device is affected by the vulnerability. Image: Cybereason.
“People tend to look down on IoT research and call it junk hacking,” Cybereason’s Yoav Orot wrote in a blog post about its findings. “But that isn’t the right approach if researchers hope to prevent future Mirai botnet attacks. A smart (insert device here) is still a computer, regardless of its size. It has a processor, software and hardware and is vulnerable to malware just like a laptop or desktop. Whether the device records The Walking Dead or lets you watch your cat while you’re at work, attackers can still own it. Researchers should work on junk hacking because these efforts can improve device security (and consumer security in the process), keep consumer products out of the garbage heap and prevent them from being used to carry out DDoS attacks.”
The discoveries by SEC Consult and Cybereason come as policymakers in Washington, D.C. are grappling with what to do about the existing and dawning surge in poorly-secured IoT devices. A blue-ribbon panel commissioned by President Obama issued a 90-page report last week full of cybersecurity policy recommendations for the 45th President of the United States, and IoT concerns and addressing distributed denial-of-service (DDoS) attacks emerged as top concerns in that report.
Meanwhile, Morning Consult reports that U.S. Federal Communications Commission Chairman Tom Wheeler has laid out an unexpected roadmap through which the agency could regulate the security of IoT devices. The proposed certification process was laid out in a response to a letter sent by Sen. Mark Warner (D-Va.) shortly after the IoT-based attacks in October that targeted Internet infrastructure company Dyn and knocked offline a number of the Web’s top destinations for the better part of a day.
Morning Consult’s Brendan Bordelon notes that while Wheeler is set to step down as chairman on Jan. 20, “the new framework could be used to support legislation enhancing the FCC’s ability to regulate IoT devices.”
Tags: 888888, Amit Serper, CVE-2015-7755, Cybereason, internet of things, IoT, Johannes Greil, Juniper ScreenOS Backdoor, Lior Div, mirai, SEC Consult, SNC Toolbox, Sony IPELA Engine IP Cameras

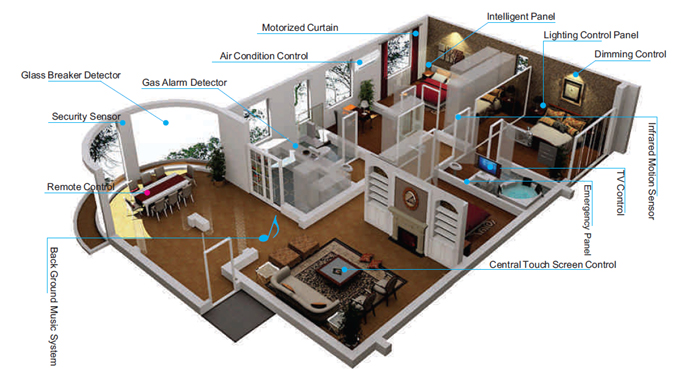
Safe and sound at home...
Imagine this scenario. Your son has come back home from school and the front door is locked. He calls you and you are able to unlock the door through your phone to let him in. Sounds bizarre? Well, not really. This is what a new age home security solution can do. An important aspect of home automation, security solutions is fasting gaining ground as the most preferred smart home solution.
Solutions galore
Single sensor alerts, standard security system alarms, wireless security cameras, Digital Video Recorders (DVR) and recording kits are a few new solutions for home security in the market. Artificial Intelligence and deep learning technology-enabled surveillance cameras, thermostats and smoke alarms are some of the new age home security solutions in the market. These help send automated alerts to home owners via email, push notifications, motion sensors, mobile app connectivity and enable the control of security systems from anywhere around the world through smartphones, tablets or laptops and cloud stored data to access at any given time.
Pankaj Tyagi, division manager, Renewable Energy Division, 3M India Limited, says, “Window films are one of the new additions to home security solutions. Hurricanes, tornadoes, severe winds, bomb blasts and earthquakes can cause glass to shatter and send shards flying, especially in high-rise buildings. During these disasters, safety and security window films keep flying glass from harming inhabitants, and in many circumstances, help keep out wind and rain.”
Tech talk
The market for home security solutions today is continuously evolving and includes monitoring options that accentuate user experience and allow for real-time tracking. Fibre to the home (FTTH) is revolutionising communication and security with the use of fibre optic cables for delivery of multiple advanced services such as telephone, broadband, Internet and television.
“Fibre optic cables ensure superior Internet speeds supporting next generation services like video on-demand and home automation that adds value to the life of residents. In terms of security, this technology enables integrated video-based visitor management system through which residents can track a visitor right from the gate of the township right up to their doorstep. The radio frequency identification (RFID) system is capable of managing the movement of the car. For instance, if a resident is out of town s/he can disable the RFID which will block the car at the entrance. This gives an extra layer of defence against any potential intruders,” says Surendra Hiranandani, chairman and managing director, House of Hiranandani.
Since the late ‘90s, instrumentation of homes has been happening with conventional burglar alarm systems, CCTV systems and electromagnetic (EM) locks. It had the basic limitation that the systems were not interconnected. “With change in technology, the concept of security has changed. Technology-based security that can be integrated and remotely accessed has become an essential part of our homes and personal life. From being discrete systems, home security systems have now converged,” opines a spokesperson from Tenon Group of Companies.
The specifics
Automation is a step forward to the term called ‘Internet of Things’, in which, everything has an assigned Internet Protocol (IP) address and can be monitored remotely. The system provides the ability to schedule events for the devices on the network. Ajay Agarwal, partner, Geopreneur Design Studio, says, “Intrusion alarm system for windows, doors, compound walls, car parks include CCTV cameras, video door phones, electrically and electronically controlled locks and latches, and digital locks which can be controlled by passwords, smart cards, thumb input-impressions etc.”
In control
One can control the entire home security by means of a combined in-built monitoring system or digital technology. It involves the integration of technology in home security. “This modern home security solution comprises switches and sensors connected to a central hub called ‘gateway’ by which the entire system is controlled with a user interface that interacts with smart phones, tablets, web interfaces and wall-mounted terminals. As a result, the user can manage everything from anywhere, using their smart devices through the Internet,” says Akhil Kumar Sureka, managing director, Sarvome Developers.
Avinash K Gautam, CEO, Silvan Innovation Labs adds, “Smart sensors detect events like door intrusion, unwanted motion, LPG gas leakage, fire and wet floors. A smart gateway to sense these sensors decide when the triggering of a sensor can be considered as a real risk, and interface with a central monitoring system for systematic logging of events and centralised monitoring. Smart cameras allow you to check out visually the situation in your house and lastly, a centralised monitoring system monitors the status of your house.”
Integrating technology
The best part of home automation solutions is that the new technology can be easily installed without much intervention as most of the products are wireless. So, one does not have to worry about extensive wiring and networking.
“For example, wireless camera systems only have to find the points of placement to cover areas like doors, garage, windows etc and mount camera on the desired location, both indoors as well as outdoors. Most of the technology products for home security are Wi-Fi enabled. We can download the concerned mobile app in our smart phone and can directly surveillance and control the entire home security system. These home security products also have a feature of cloud-stored data and are hassle-free. They have battery as well as plugged cable installation for outdoors,” says Prasoon Shrivastava, CEO & founder, Helpmebuild.
The security requirement in the real estate sector, largely for its three categories of buildings — retail, residential and commercial demand a diferent security protocol because their environments differ.

Next-Gen Bluetooth Is Here: Faster and Key for Internet of Things
The Bluetooth Special Interest Group (SIG) announced yesterday that it has adopted specifications for Bluetooth 5, a standard that is expected to begin appearing in new devices within two to six months. The latest specifications enable connections at up to four times the range and twice the speed of the previous version of Bluetooth, the group said.
With broadcasting support for as much as eight times the message capacity of Bluetooth 4, the new standard will also help users and developers deploy "improved and more context-relevant solutions," according to the Bluetooth SIG.
Support for More than 10B Devices
Bluetooth 5 will help drive further development of the IoT by enabling reliable connections and easier adoption of beacon technology, Mark Powell, executive director of the Bluetooth SIG, said yesterday in a statement. That, in turn, "will decrease connection barriers and enable a seamless IoT experience," he added.
With its longer range, Bluetooth 5 will make it easier to provide connectivity across entire homes and other buildings, Powell said. It will also support "new use cases for outdoor, industrial and commercial applications."
The wireless technology already supports an installed base of more than 10 billion devices around the world, according to the Bluetooth group. The Bluetooth SIG predicts that number will increase to nearly 14 billion devices by 2020, with one in three new wireless products shipping with Bluetooth technology by that time.
New Opportunities in Smart Homes, Emerging IoT
The release of Bluetooth 5-enabled devices in 2017 will represent "another milestone" in the standard's development as a technology for IoT connectivity, according to a market report released last month by ABI Research.
"While smartphones and audio accessories remain Bluetooth's largest markets, the technology is becoming more attractive to low-power IoT applications," analyst Andrew Zignani said in statement accompanying the report's release. "Though Bluetooth still faces strong competition from the other standards, mesh networking will enable new opportunities for the technology in the smart home, building automation, and emerging IoT markets in which robustness, low latency, scalability, minimal power consumption, and strong security are all additional critical requirements."
Bluetooth 5 features updates designed to "reduce potential interference with other wireless technologies to ensure Bluetooth devices can coexist within the increasingly complex global IoT environment," according to the Bluetooth SIG.
By doubling speed while continuing to support low power consumption, Bluetooth 5 will enable faster data transfers for medical devices, security systems and other applications where speed is a priority, according to the group. The low energy demands of the technology also makes it ideal for coin cell batteries or energy-harvesting devices that need to run for long periods of time on limited power supplies.
Suddenly hot smart home devices are ripe for hacking, experts warn
Experts expect the number of attacks on the Internet of Things (IoT) will likely increase in 2017. IoT includes devices like webcams, DVRs and connected thermostats that make life easier for homeowners, but are susceptible to cyber-intrusions.
These gadgets add conveniences like locking your door or shutting off the lights all from a smartphone app, but they come with certain risks, experts warn.
"The sharks have smelled the blood in the water and they're now circling to use your IoT device for further attacks," said James Lyne, global head of security research for Sophos, a U.K.-based cybersecurity company.
The concerns about technological vulnerabilities come as experts say smart home devices are hot gifts this holiday season. The growing reach of smart devices makes the dangers more acute, some say.
"I think we're going to see real strength in the Internet of Things and it's not just your thermostat, it's going to be everything in your house, your refrigerator, your washing machine, your dishwasher," Jan Kniffen, a consultant specializing in retail and CEO of J. Rogers Kniffen Worldwide, said on CNBC's "On The Money" recently.
Despite the proliferation of smart gadgets, Kniffen suggested consumers were either unaware or unconcerned about hacking risks—and not taking appropriate measures to prevent them.
In October, hackers took over 100,000 IoT devices and used them to block traffic to well-known websites, including Twitter and Netflix.
"This is just the beginning of cybercriminals finding ways to creatively use the internet of things. Almost like a test attack," Sophos' Lyne said.
The type of attack is known as a distributed denial of services (DDoS).
"To translate it to the physical world, you know when you go to a shop you've got a revolving door," Lyne continued. "It's like getting a ton of your friends to go to this shop and all run around in circles in the revolving door, so no actual customers can get inside," Lyne said.
While the attack is not believe to have cause any lasting damage, sometimes DDoS attacks are used to cover more damaging attacks.
"We've seen cybercriminals previously launch these big attacks against websites to draw everyone's attention in, whilst in the background they conduct a more sinister attack of a financial nature," said Lyne.
"I think all of us, from industry to individuals, to government are going to have to up our game in terms of making sure these devices are safe from the very real threat of cyber hackers."
-Mark Warner, U.S. Senator
This was the first wide-scale attack that used these devices, but as more a more consumers add the devices to their home, attacks are expected to grow.
"We're going to go from 12 billion devices we currently have, to over 30 billion devices by 2020, all interconnected. That's going to add to the ease of our life but if all these devices are easily hacked into it could mean we could have a whole new host of security concerns," said Sen. Mark Warner, a Virginia Democrat. Warner is a member of the Senate Select Committee on Intelligence and co-founder of the Senate Cybersecurity Caucus.
Smarthome devices are vulnerable because of poor programming. "Devices like these often come with a really bad and easy to guess username and password," Lyne said.
Cybercriminals then take over IoT gadgets by searching the web for those with default passwords. Guessing the password allows the hackers to take over the device and harness its processing power for attacks.
Accordingly, a closed caption television camera or DVR "is enough of a reason to attack you so that you can be useful to attack other people. You are a target," said Lyne.
Many of the devices used in the October attack were recalled by Chinese manufacturer, Xiogmai. But according to Lyne, many vulnerable devices are still for sale.
"Chances are right now if you're buying an Internet of Things device, you're more likely to be buying something insecure, than secure," he said.
To help manufacturers, the Department of Homeland Security released strategic principles for IoT just last month, calling it "a matter of homeland security."
However, the principles are not binding or regulatory and experts told CNBC more needs to be done. "To the vendors, you've got a very small window. The cybercriminals have noticed the abhorrent lack of security," said Lyne.
"I think all of us, from industry to individuals, to government are going to have to up our game in terms of making sure these devices are safe from the very real threat of cyber hackers," said Sen. Warner.
To protect yourself, Lyne recommends first deciding if you really need a smart home device in the first place. "You should ask yourself seriously, do you want this device in your home right now, while the industry takes action to fix these problems," he said.
If you do use or buy IoT devices, you should change the default password and make sure to update the software.
"If you do have one of these devices, make sure you're running the latest version of the software, because lots of manufacturers have issued fixes," Lyne said.

This technology may make credit cards and mobile transactions hack-proof
The technology, which allows fast, automated identification of physical objects, is also a staple for many industries - factories and warehouses use it to track inventory and manage supply chains, pharmaceutical companies deploy it to track drugs, and courier services use it to tag deliveries.
"A security breach in RFID applications would leak valuable information about physical objects to unauthorised parties," said Li Yingjiu, associate professor at the Singapore Management University (SMU).
Since RFID tags work by broadcasting information to electronic RFID readers, security breaches can occur if hackers eavesdrop on this conversation, and manage to gain access to or tamper with information.
To protect communications between tags and readers, researchers are designing and testing new RFID protocols with enhanced security features.
These strategies include making the protocol's output unpredictable, making two tags indistinguishable to the hacker, and preventing hackers from obtaining useful information even if they manage to interact with the tags.
In addition, there are many instances where sharing of RFID information - between suppliers and retailers, for example, or between various components of an Internet of Things - would have obvious benefits, said Li.
However, without appropriate security controls, most companies would be reluctant to make valuable data readily available.
To address this problem, researchers are also designing improved access control mechanisms that protect RFID information when it is shared on the internet.
We in fact carry RFID around in our pockets - mobile payment systems use a specialised form of the technology.
Given our increasing reliance on smartphones for everyday functions - banking transactions and contactless payments, for example - mobile security has become an area of critical importance.
Cops to increasingly use digital footprints from IoT devices for investigations
The police are being trained to look for “digital footprints” – IoT gadgets that “track or record activities” which might prove or disprove alibis and witness statements as well as record what occurred during a murder victim’s final moments.
Cops will be relying on evidence from smart devices which spy on you – such as internet connected refrigerators, light bulbs, washing machines, vacuum cleaners, coffee makers and voice-controlled robotic assistants.
Stokes explained:
“Wireless cameras within a device such as the fridge may record the movement of suspects and owners. Doorbells that connect directly to apps on a user’s phone can show who has rung the door and the owner or others may then remotely, if they choose to, give controlled access to the premises while away from the property. All these leave a log and a trace of activity.”
Think about that while perusing products on display at CES 2017 as this has the potential to go much further than cops tapping into smart fridges and doorbells. For example, a robotic vacuum cleaner such as Unibot, which will be shown off at CES 2017, comes equipped with a security camera so it can send owners pictures and videos in real time in case it detects “unusual signs in its peripheral vision.”
All manner of smart items meant to provide convenience could also potentially be used to narc on you – used by the police to gather evidence. Some folks won’t be bothered by that since they willingly carry a smart phone which can double as a surveillance device; phones are frequently targeted by law enforcement during investigations.
Millions of people already wear wearables, but in the future, even a person’s clothes will be able to provide location data. There are already some smart clothes, such as “vibrating” jeans, which connect to a smart phone and vibrate on one side or the other in order to give GPS map directions without the user needing to whip out her phone.
A self-driving car, for example, would have location logs, but hopefully couldn’t be used against riders such as by locking the doors until police arrived to collect the person inside.
While most people don’t yet have a smart refrigerator, many do have smart TVs and most smart TVs include a camera and microphone. Voice control assistants such as Amazon’s Echo and Google Home, are quickly gaining popularity. This year at CES, there will be a plethora of products built to integrate with popular voice control assistants and even new voice control bots.
Not that all smart voice-controlled assistants correctly understand what is asked of them – as one family found out after a little boy asked their new Amazon Echo Dot to play “tickle tickle.” Alexa thought the child wanted porn and started to comply before the parents freaked out and shut her down.
The smart meter, Amazon Echo and a murder investigation
The idea that police would use data provided by IoT devices is nothing new. Police in Arkansas are pressuring Amazon to hand over data from an Echo device; the cops think some of the recorded audio data sent to the personal assistant “Alexa” may be helpful for their murder investigation. Amazon did not comply – other than sending the suspect’s purchase history.
Bentonville police detectives have already used IoT data – data from a connected water meter. The cops think the massive spike in water usage on the night of a murder may indicate the hot tub and patio had been hosed down to wash away blood evidence.
When cops start looking for “digital footprints” in IoT gadgets, it supposedly won’t be like when the cops seize a hard drive, laptop or computer for an indefinite period during an investigation. Stokes said the smart devices wouldn’t need to be seized and hauled off. Instead, investigators will use a “digital forensics kit,” which is yet to be developed, to download data and analyze microchips at the scene.

Now a toothbrush with Artificial Intelligence to improve oral care
Kolibree, a tech company focused on connected solutions in oral health, arrived with a toothbrush at CES 2017 named Ara that is embedded with Artificial Intelligence (AI).
With an eye on disease prevention and wellness, Kolibree states that the toothbrush has deep learning algorithms embedded on a low-power processor. Raw data from the sensors runs through the processor, which learns one’s brushing habits and refines it the more it is used. In other words, the more you use it , the smarter it gets.
Kolibree Ara has been designed to work both online and offline. The toothbrush can store all the information through motion sensors in offline mode, and it syncs up with the app when next time user loads it. You will also get a weekly e-mail report that will show how well you have brushed over the last seven days.
Developed for adults, Ara’s testing will take place in USA and Europe and aims to show how AI can change people’s daily behaviors and improve oral care.
And who knows, maybe someday brushes like these could put dentists out of business.

This smartwatch ticks for your personal safety
“Big players have tried to replicate a smartphone into a smartwatch,” said Neravati, founder and chief executive of the Hyderabad-based wearable tech startup. “We wanted to create a safety product which is fast and intuitive and has features which are additional to what smartphones have to offer.” This is where, he believes, the product is different. The smartwatch, along with features for fitness, health and nutrition, has gesture recognition, which can be used if the user’s security is compromised at any point. “It will send an amber alert to the person who is registered as the point of contact,” said Neravati.
The bootstrapped company has sold close to 300 smartwatches since the product was launched six weeks ago. With an idea of keeping the device fun, easy-to-use and intuitive, Neravati says gesture recognition features can be used in multiple areas and can lead to a touchless interaction in Internet of Things, virtual reality, gamification and healthcare, among others. “The device has contextual intelligence. So the same gesture performs a different action based on the device it is being paired with,” he said. The Hug smartwatch can be paired with a music player, laptop, or a Philips smart bulb, among others. Hug Innovations is also in talks with Telangana, Karnataka and Maharashtra governments to integrate the security feature of its technology into the bullet-proof Rakshak vehicles.
The wearable devices market in India grew 41.9% in the second quarter of the current fiscal over the first quarter when around 400,000 devices were sold, according to International Data Corporation’s wearable device tracker. However, the worldwide smartwatch market declined in shipment volumes by nearly 52% in the third quarter of 2016 as compared to the same quarter in 2015. Experts say the smartwatch and wearables market is over-competitive. “Microsoft had come out with a band, which is dead. Pebble has shut shop and some of it has been acquired by Fitbit,” said Vishal Tripathi, research director at technology research firm Gartner.
Tripathi thinks that in the case of the Hug smartwatch, the personal security feature is attractive, but is not certain if it is compelling enough for a customer to switch from a Fitbit. He also points to the practical challenges of a Hug smartwatch. “I think fitness bands still have their charm. While the SOS feature will add value. It has various practical challenges,” he said. “However, by providing an attractive price, more accuracy than existing bands, the additional features may garner customer’s attention.”

Now Zoomcar’s analytics platform to help reduce road accidents
Greg Moran, CEO, Zoomcar points out that the name “Cadabra” is not just a device but a platform. It is fixed with Bluetooth, 4G cellular connectivity and tracks level of fuels in the cars, the position of clutch, sudden braking, hard acceleration, engine health and sharp corner turns.
Greg claims that in the near future, this device will also get over the air updates which will help them add more functionality to the entire experience.
“The real time insights about your driving and that’s what is going to make you a better driver. It can help you save fuel cost, reduce the service and maintenance cost, help you to avoid accidents and that’s a really important one because there’s a very high correlation, it’s very predictive actually, if you are inherently abusing the brakes, not using the clutch the right way, you’re many times more likely to get into a major accident,” says Morgan.
Cadabra as claimed by Zoomcar is integrated into the parent Zoomcar app and will help Greg and team review and rate trips, keep a track of the score and give real time tips to driver to improve the their driving skills. “The more data the car generates, the more responsive Cadabra becomes. This opens up many possibilities in the months ahead,” says Morgan.
This analytics platform was built internally by a team of 30-35 people in India who come from a background of statistics and computer science.

China to develop prototype super, super computer in 2017
If successful, the achievement would cement its place as a leading power in the world of supercomputing.
The Asian giant built the world's fastest supercomputer, the Sunway TaihuLight machine, in June last year, which was twice as fast as the previous number one.
It used only locally made microchips, making it the first time a country has taken the top spot without using US technology.
Exascale computers are even more powerful, and can execute at least one quintillion (a billion billion) calculations per second.
Though a prototype was in the pipeline, a complete version of such a machine would take a few more years to complete, Xinhua news agency cited Zhang Ting, application engineer at the National Supercomputer Center in the port city of Tianjin, as saying.
"A complete computing system of the exascale supercomputer and its applications can only be expected in 2020, and will be 200 times more powerful than the country's first petaflop computer Tianhe-1, recognised as the world's fastest in 2010," said Zhang.
The exascale computer could have applications in big data and cloud computing work, he added, noting that its prototype would lead the world in data transmission efficiency as well as calculation speed.
As of last June, China for the first time had more top-ranked supercomputers than the US, with 167 compared to 165, according to a survey by supercomputer tracking website Top500.org.
Of the top 10 fastest computers, two are in China and five in the US as of November, the ranking said. Others are in Japan and Switzerland.
China has poured money into big-ticket science and technology projects as it seeks to become a high-tech leader.
But despite some gains the country's scientific output still lags behind, and its universities generally fare poorly in global rankings.

Australia to replace passports with facial recognition and Fingerprints
The Department of Immigration and Border Protection is seeking tenders for a self-processing system to be introduced later this year, Australia's ABC News reported.
The system will use fingerprints, iris or facial structure recognition at major air and sea ports.
Immigration Minister Peter Dutton said the aim was for more than 90 per cent of passengers to avoid paperwork or manual processing by staff.
"In many cases that will mean people, whilst they'll still have to carry their passport, may not have to present their passport at all in the long term," Dutton said on Sunday.
"But in the immediate term, this will make it easier, it will make it quicker, for people going in and out of our airports."
Under the new system, the existing SmartGates that scan passports electronically - introduced less than 10 years ago - would be retired.
Dutton said the $78 million upgrade would also boost security at the nation's borders by making it easier to detect threats, ABC News reported.
He said cutting down processing times for travellers was also likely to boost tourism.
Forty-million air and sea travellers were processed by the Australian Border Force in the 2015-16 year, the Guardian reported citing an official report.

India leaves America far behind in innovation with its digital push
Though few people in the West know of Aadhaar, it has been the largest and most successful information technology project in the world. There was widespread scepticism about whether a billion people could be provided with a verifiable digital identity, yet it has occurred, in a short span of six years. Hundreds of millions of people who were doomed to live in the shadows of the informal economy can now participate as equals in the global economy. Thanks to Jan-Dhan Yojana, they also have bank accounts; these already have Rs 69,000 crore in deposits.
The reason investors are pouring billions of dollars into technologies such as bitcoin is because it provides a secure way of linking users and recording a transaction.But bitcoin requires massive, wasteful computing resources to do what is called mining: transactions' mathematical verification. And this complex computing infrastructure also needs constant improvement.
The simple design of India's digital payments infrastructure, Unified Payments Interface (UPI), allows banks to transfer money directly to each other based on an Aadhaar number or, a mobile-phone number plus pin. Yes, this doesn't have the anonymity of bitcoin, but I would argue that anonymity is mainly for money laundering and tax evasion -which need to be eliminated. There is almost no overhead in UPI, and transactions happen within seconds rather than the 10 minutes that bitcoin takes. In the US, users pay an indirect tax of 2-3% on consumer transactions because of the use of credit cards. Companies such as Visa, Mastercard and American Express don't even manage the money or provide banking services, all they do is to act as an intermediary between banks. The merchant has the responsibility of verifying the identity of a customer.With UPI, India doesn't need credit cards or middlemen, it can build the next generation of finance.
The instant and non-repudiable proof of identity that Aadhaar's know-your-customer technology -e-KYC -provides, gives India a big advantage. Most people in the US have drivers' licences and social security numbers. But these are not verifiable with biometrics or mobile numbers, so complex verification technologies need to be built into every financial system. Indian entrepreneurs building applications don't need to worry about all this.
Going beyond money, India Stack provides a digital locker through which to store and share personal data such as addresses, medical records, and employment records.With this, the government is providing a public service that is the digital equivalent of roads and electricity. I don't know of any other country that has anything comparable.
Nobel Prize-winning economist Joseph Stiglitz said in Davos that the US should follow Prime Minister Narendra Modi's lead in phasing out currency and moving to ward a digital economy, because it would have "benefits that out weigh the cost". Speaking of the inequity and corruption that is becoming an issue in the US and all over the world, he said: "I believe very strongly that countries like the United States could and should move to a digital currency so that you would have the ability to trace this kind of corruption".
Yes, India is ahead and America can learn from it.
(The writer is a fellow at the Carnegie Mellon University Engineering at Silicon Valley)
Newsletter
Sign Up for Monthly Newsletter
Recent Tweets
CONTACT US
Crux Center for Security
Research and Events (CCSRE)
3rd Floor, Tower-B, Unitech Cyber Park
Sector 39, Gurugram,122022
0124- 4207903, 05, 06
Copyright © 2016 Crux Center For Security Research And Events (CCSRE) | All Right Reserved
